Project tittle : Development of an interactive computer based training that allows students to learn Bourne Again Shell (BASH) scripting language.
Main reason for the project is the lack of such products. Moreover the end product is also to help students undertaking Operating Systems module at University of East London and is expected to be used as a part of a practical sessions of that module, as well as any interested world wide web user
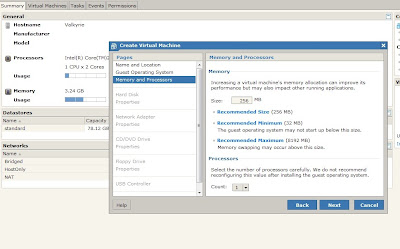
The application has been build using Adobe Flex Builder 4 and Actions Script 3.0.
The session were .ppt files converted into .avi and converted once more into .swf format which has been implemented in Flex.

The scope for this project is excellent and there is still plenty that is planned to achieve in the future. After all the bugs are fixed and application is stable, rest of the sessions are ready to be developed. That includes some interesting sessions such as Network Security or Firewalls where BASH would be used to automate some advanced tasks. Another crucial thing would be to expand console component not only to accepts strings as ‘cd /home/ and then while accessing ‘pwd’ to display that current directory but far more than that. A console that simulates unix text editor and allow user to write scripts and analyses them. At some point console component would have allocated disk space so that it can emulate file system and user can create, copy and move files which would be very useful in the session where the task is to move the users from one volume to another.
Moreover users could register on the website and keep record of the sessions they have completed and maintain the same emulated environment with their files etc. That will require additional disk space depending on the number of users.
Another aspect to enchant is to index the page with Google and do searching optimization tasks to make the web based training popular on the World Wide Web.
Android is gaining popularity and recently released 3.0 Honeycomb software designed especially for tablets. Tables average screen size is 10’inch and they have flash support (except Apple) therefore the application could be optimized towards tables if needed. (Geere, D. 2011)
Moreover Adobe Air package offers a possibility for converting this already made application to Adobe Air , that means that the application could be downloaded as a standalone application and run even without network connection.
New ideas for further enchantments are coming every day. There seem to be no ending.
Personal Reflections
To conclude the project has been successful even though the result is below personal expectation. Based on the users feedback there is still plenty to improve such as console component and other bits and pieces. There is still few bugs that were found during testing that need to be fixed before proceeding towards creating of more advanced sessions. Overall look of the web based training is pleasurable for the eye and attracts new users, therefore there is a big scope for future enchantments listed above. Due to some constrains there was less time for this project than expected and deadlines were really tight nonetheless successful. If there was anything that I would change with the application is better use of Action Script libraries and use classes such as event. COMPLETE rather than to start timers for each session. The attempt was made to make different way to make it work however Flex Builder version 4 has not been that stable. Time is needed for evaluation and sorting out the application component by component, which eventually will become superb.
Personal Development
Throughout the project I have learnt how to work really hard and meet my deadlines and especially how to use my time efficiently. I have learnt Bourne Again Shell scripting language, Flex syntax and ActionScript 3.0 which is a massive progress for me in such a short period of time. I have also developed the ways to think outside the box while quick research on PowerPoint and then conversion to video and then to flash. It was also very good for me to use these tools. Flex Builder 4 has been designed with the same GUI as eclipse did so it’s much easier for me now to write code in Java or PHP using eclipse after knowing all the tricks and being familiar with the interface and functions.
Sample of the code for session component.
protected function session1_clickHandler(event:MouseEvent):void
{
//clear interaction panel
interaction.removeAllElements();
// start timer and listener
var timer:Timer = new Timer(205000,1);
timer.addEventListener(TimerEvent.TIMER, ses1con1);
timer.start();
// add session .swf file to the loader.
interaction.addElement(loader);
loader.source="sessions/session1.swf";
// play mp3 for the session
snd = new Sound(new URLRequest("audio/session1.mp3"));
snd.play();
}
protected function ok1_clickHandler(event:MouseEvent):void
{
// victory mp.3 play for guessing correct answer
victory.play();
// display that correct answer was chosen
Alert.show("Correct answer! Keep it up!","Good",Alert.OK);
// clear interaction panel
interaction.removeAllElements();
interaction.addElement(loader);
// load session, sound and timer
loader.source="sessions/session1_1.swf";
snd = new Sound(new URLRequest("audio/session1_1.mp3"));
var timer2:Timer = new Timer(95000,1);
timer2.addEventListener(TimerEvent.TIMER, ses1con2);
timer2.start();
snd.play();
}
I would like to thank:
Mike Kretsis who is senior lecturer at University of East London and my project supervisor, without whose help and support throughout, this project would not have been possible.
My lovely partner Margareta for all the support and care she gave me.
All the participants who agreed and evaluated this project, even more for those who were critical.